Configuring SSH key usage log collection
For Trust Protection Platform to receive SSH key logs from the agents, you have to configure settings in SSH Protect. The agentcollects the SSH logs by using the TCP port 689 and delivers the SSH logs to Trust Protection Platform according to the assigned work schedule.
To configure settings
- From the SSH Protect menu, click Clients > Client Group Settings.
-
Select and click an existing group of servers from where you want the SSH logs collected for generating the report.
The server machines must have agents installed on them.
NOTE For more information on group membership, see Defining group membership criteria .
- Under the Groupname\Members dialog box, click Work.
-
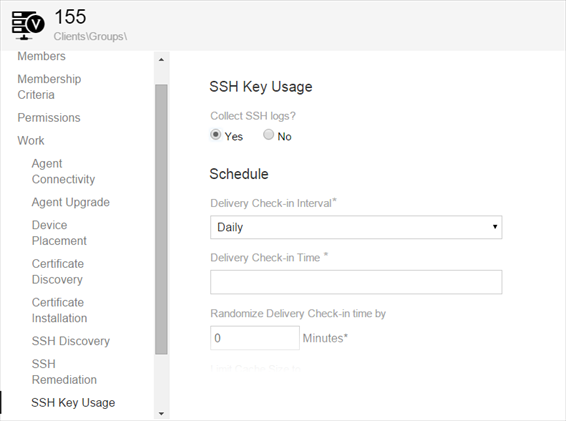
Under Work, click SSH Key Usage.
-
Under SSH Key Usage, select Yes.
BEST PRACTICE The schedule should be frequent enough to ensure up-to-date analytics and avoid agent buffer overflow. Ensure that the Agent delivers the logs before the record size is greater than the agent buffer size that is specified by synchronizing the schedule with average key usage volumes.
- Under Schedule, in the Delivery Check-in Interval list, select the frequency for delivering the SSH key logs.
-
Select Delivery Check-in Timeto select the hour of the day when you want the agentto deliver the SSH keys.
NOTE When you select Hourly as the Delivery Check-in Interval, the Delivery Check-in Time field is hidden.
-
In the Randomize Delivery Check-in Time (Minutes) field, specify a window of time to be used by all agents for checking in with Trust Protection Platform.
The purpose of this option is the same as the randomized check-in interval for SSH agent check-ins and helps to reduce network and system load.
-
Enter the number of SSH key usage logs to store under Limit Cache Size to.
NOTE Cache size sets the agent side buffer.
- When you are finished, click Save.
What's Next
Once sufficient SSH log data is collected by Trust Protection Platform, you can view the Analyzing the Key Usage data report.