Analyzing the Key Usage data report
Key usage data report provides and information that will help you analyze the SSH keys log data collected and correlated with key inventory in Trust Protection Platform.
The key usage report will be generated after you have configured the SSH key usage work in Aperture and the agent has transmitted the key logs to Trust Protection Platform.
The generated report contains the SSH key usage data collected by Trust Protection Platform. The data can be analyzed and steps can be taken to detect and remediate stale keys, rotate old keys, identify keys from unknown clients and, if required, add self-service keys.
EXAMPLE SSH key usage records are created after a thorough matching process where the SSH key usage data is correlated with existing SSH keys in Trust Protection Platform. The SSH records are matched with the SSH keyset inventory data by comparing the device IP address, fingerprint, and account information. Based on the comparison, alerts are generated for keys that are not tracked in SSH Protect and keys accessed from clients that do not have a corresponding private key tracked in Trust Protection Platform. The last date on which the keys accessed the server is also listed.
Viewing the Key Usage report
-
From the SSH Protect menu, click Reports > Key Usage.
The SSH key usage report is generated and includes the following columns:
- Server – the server to which the clients connect.
-
Client – the IP address or device which is connecting to the server via SSH.
NOTE The server, client, or fingerprint can link to actual device or keyset in Trust Protection Platform if the matching process finds a match.
- Server Account – the account information on the server that is accessed.
- Fingerprint – the SSH key's unique fingerprint.
- Last Access – this date indicates when the key was last used to gain access. This information can help identify stale or unused keys.
-
Alert – provides information on keys untracked in SSH key manager and keys used from unknown client.
TIP Using the alert information in the key usage report, you can take appropriate action on at-risk keys. For example, in case of untracked keys, you can install agents on those clients so that the keys will be found during key discovery.
For unknown clients where there is no client information (IP address is not recorded in Trust Protection Platform) and the private key is not registered, you can add a self-service key to indicate that accessing the server from unmanaged machines is valid or rotate the keys so that the clients don't get newer versions of the keys.
Sometimes the scan may not discover keys and require the scan settings to be adjusted. Refer to the section Analyzing and fixing SSH violations for more information.
NOTE The term untracked in this context does not mean that Trust Protection Platform is unaware of the key. Untracked Keys are keys identified in key usage logs but not discovered and managed in the SSH key inventory.
Filtering the Key Usage report
You can filter the results of the SSH key usage report using custom filters. These filters will help you identify high risk keys based on your search criteria.
For example, you can filter on the following fields:
- Server Name
- Account
- Client Name
-
Alert
-
Fingerprint
If you want to save the filters you've added to the SSH key Usage Report, you can click the Generate Report button, which will create a custom report on SSH Key Usage based on the filtered data. For more information on custom reports, see Creating customized reports—overview.
About the last accessed date for keys
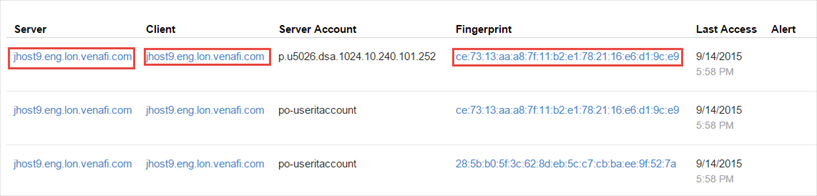
The SSH Key usage report provides information on the last accessed date for all keys. In the report, if the Server, Client, and Fingerprint show active links, click on the link to view the client or server details for the keyset.
The following screen shows keys with all three fields (server, client, and fingerprint) linking to key details.