SSH policy settings details
There are a broad range of policy settings that you can configure for SSH keys. The sections below correspond to the page tabs on the policy settings page.
The General policy settings contain the following sections:
General
|
Field Name |
Description |
|---|---|
|
Security Level |
Choose how the ssh keys will be managed by Trust Protection Platform.
If changes are made to the keys outside Trust Protection Platform, what happens will depend on the management type. For more information see Remote changes to SSH keys. |
|
Allow Agentless Discovery and Remediation |
When set to Yes, an agentless SSH connection will be allowed to discover and remediate SSH keys. NOTE This setting can take up to 15 minutes to fully take effect. |
| Allow Adaptable Discovery |
Adaptable SSH Key Discovery is a special type of agentless discovery that uses custom PowerShell scripts to access any device of any operating system in your network. Even though Adaptable SSH Key Discovery is a type of agentless discovery, this setting allows the adaptable type of agentless discovery to work, regardless of whether other agentless discoveries can also work. For more information about Adaptable SSH Key Discovery, see About Adaptable SSH Key Discovery NOTE This setting can take up to 15 minutes to fully take effect. |
|
Contacts |
Allows you to select the identities (users or groups) that will be used as points of contact for SSH keys in this folder. |
| Allow Symbolic Links |
When set to Yes, file operations are allowed to be performed on symbolic links (symlinks). Note: So-called "symbolic link attacks" are a significant risk factor so this option should be set to No unless you have the expertise and a special need to enable it. You can choose to flag or not to flag the use of symbolic links as a policy violation by using the option described in the Flagging items section. |
|
Approver(s) |
Allows you to select the identities that will be used to approve SSH key workflow actions for keys in this folder. |
|
Encryption Key |
Select the encryption key you want to use. Trust Protection Platform allows you to specify custom encryption keys for SSH keys that are stored in the system. By default, all keys are encrypted for storage using either the software encryption key, or a hardware key stored in an HSM. All new keys added to the folder will use the new encryption key. If you are storing certificates and SSH keys in the same policy folder, you can specify different encryption keys for SSH keys than you use for certificates. |
|
Environment |
Specifies the value used to validate that the keysets in this folder contain key instances under the same environment. This allows you to define environments for devices and folders, and if authorized keys and private keys are in separate environments, then a risk can be shown in SSH Protect. |
| Maximum Authorizations Allowed Per Keyset | When generating the SSH Authorized Clients report, having a large number of authorizations for a single keyset can reduce performance, and might not be useful for you. By default, Trust Protection Platform restricts the maximum number of authorizations displayed on the SSH Authorized Clients report to the value set here. Default is 50,000 authorizations. |
Key Settings
The Key Settings section allows you to specify default information about the keys and certificates stored in the folder.
NOTE The Allowed Algorithms field specifies which algorithms can be selected for this policy and its child policies. Keys discovered that do not match the allowed algorithms are flagged with a policy violation.
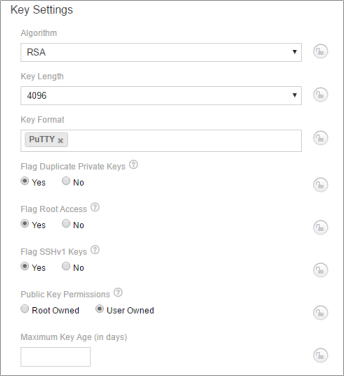
Specifying settings for algorithms
You can specify any of the supported algorithms including:
- EdDSA curve 25519 (OpenSSH and PuTTY)
- NIST curve P-256, NIST curve P-384, and NIST curve P-521
- RSA 1024 bit, RSA 2048 bit, RSA 3072 bit, and RSA 4096 bit
Managing SSH key generation and certificate issuance with allowed algorithms
The Allowed Algorithms field ensures consistency and compliance by limiting the selection of algorithms for SSH key generation and certificate issuance.
Here are some important points:
-
Key generation: Only algorithms specified in the Allowed Algorithms field are used for generating SSH keys.
-
Policy violations: During key discovery, any keys not matching the allowed algorithms are flagged as policy violations.
-
SSH certificate issuance:When a client submits a public key for signing, the system checks that the key’s algorithm is on the allowed list before issuing the certificate.
-
UI behavior: Restrictions in the Allowed Algorithms field apply to nested policies. If a parent policy restricts certain algorithms, these restrictions cascade to child policies.
-
API:The Allowed Algorithms field specifies which user public keys will be accepted by the Venafi Platform API for signing, thereby converting them into SSH certificates.
Using the correct settings in Allowed Algorithms enhances the security and manageability of SSH keys and certificates.
Flagging items
This section includes several options to flag items that are added to the folder even though those keys contain known security risks. These settings don't prevent keys from being added to the folder. These settings just determine whether these security risks should be flagged when keys with these risks are added to a folder.
Items flagged as policy violations display the violation status in the Risks column of the Device Inventory report.
NOTE You should always use the UI to perform actions, such as deleting a key, to remediate a key's policy violation instead of performing actions manually from the command line.
Scenarios and suggested actions
-
General example of flagging items. The SSHv1 protocol has several known security vulnerabilities. If you want SSHv1 keys to be flagged in your system when they are added, you would set this policy attribute to Yes. If you wanted to import these keys without a warning, you would set this policy attribute to No.
-
Flag Invalid Permissions: Rotate Trust. Items flagged and reported as Invalid Permissions have overly permissive permissions and too open permissions. These keys are forever compromised and unsafe. You should either rotate (replace) or delete the key. Changing permissions does not fix the risk, and the policy violation remains since the key can no longer be trusted.
Source Restrictions
If you want to set a policy for controlling access to the items in this folder based on a specific IP address or host name, you can configure those settings here.
NOTE This setting applies to authorized keys and it controls access to devices.
Select Allow Connections From or Deny Connections From, and then type the IP addresses or host names in the correct field. If inserting multiple values, separate each value with a comma.
EXAMPLE If you specify a source restriction for User 1's public key to the following:
123.245.143.*,*.mycompany.com
Then User 1 will only have access to the server where the her public or authorized key is found and if she is accessing it from a computer or host name that matches the IP address of 123.245.143.[any valid number] and from a domain name of [any valid prefix].mycompany.com.
This protects your servers in the event that a user who is no longer authorized to access your servers attempts to use a corresponding private key from a computer with an unauthorized IP address or domain.
Options
The Options section gives you additional options you can set via policy.
-
Forced Command. Using forced commands, you can limit user accounts, SSH access, and usage. Forced commands are used to enforce what is executed during an SSH connection and disallows arbitrary commands, e.g., a key pair to another system. In addition, forced commands are also discoverable during agent-based discovery.
-
Other Options. The Other Options field allows you to specify additional authorized key connection options. For each of the options listed below, they can be added only one time, and accept no parameters, unless otherwise specified.
List of keywords and corresponding vendor support Keyword SSH vendor Open SSH Tectia no-user-rc
x
no-X11-forwarding
x
x
no-agent-forwarding
x
x
no-pty
x
x
no-port-forwarding
x
x
permitopen="host:port"
x
environment="NAME=value"
x
x
cert-authority
x
principals="principals"
x
tunnel="n"
x
idle-timeout="time"
x
For more information about options, visit OpenSSH's web site and Tectia's web site.
Rotation
This feature allows you to specify the period of rotation for all client keysets in the current folder.
The Device Connection policy page contains the following fields:
|
Field Name |
Description |
|---|---|
|
Credential |
Specify a predefined |
|
SSH Port |
Specify the port to be used to make the connection for agentless connections. By default, the SSH port is port 22. |
|
Prevents multiple authentication attempts when authentication was refused by the server. If the server refuses the connection and this option is set (either here, at the policy level, or on the device settings), no further attempts to connect will be made until one of the following happens:
The term authentication failure does not apply if there was a network error that prevented the connection. It only applies when the credential was provided to the device, and the device refused to connect. |
|
|
Privilege Elevation |
Specify how the agentless account should elevate privileges. Supported options are:
Use the Other option if you need to use a custom command to elevate privileges, then select the correct Elevation Command. If necessary, specify the Privileged Credential after clicking Advanced Options. Please refer to your vendor documentation for more information on properly configuring your PAM tool. For your reference, there is an article on the CyberArk Customer Support article entitled "Info: Configuring Privileged Access Management Integration" that contains a list of the commands that are used by the agentless drivers. NOTE This feature only supports SSH management. You cannot use it for discovering or managing certificates. |
|
Enforce Host Key Checking |
Specified whether the server's host key fingerprint is verified during the SSH connection. This is a SHA-256 fingerprint of the server host key. The preferred key algorithm is RSA, followed by ECDSA. IMPORTANT If you specify Yes here, you will need to set fingerprints correctly on all devices affected by this policy. |
NOTE The policy folder also has options for configuring certificate policy settings and seeing and editing permissions information for the policy. For more details on configuring certificate policies, see Setting policy on a folder. For more details on editing permissions, see Assigning permissions to objects.