Understanding keys, keysets, and trust
A keyset is made up of keys that use the same public key hash. Trust refers to the ability to connect one account to another account, such as a user account on one computer (client) authenticating with an administrator account on another computer (server).
NOTE Keys and keysets are, of course, just one way to establish trust. The SSH protocol supports several other methods of authentication, including passwords, host-based, Kerberos, etc. Currently, Trust Protection Platform supports only the key-based method for establishing trust.
In the following diagram, Bob on Host A has a trust relationship with Alice on Host B and Frank on Host C. However, Alice on Host B does not have a trust relationship with Frank on Host C, and vice versa.
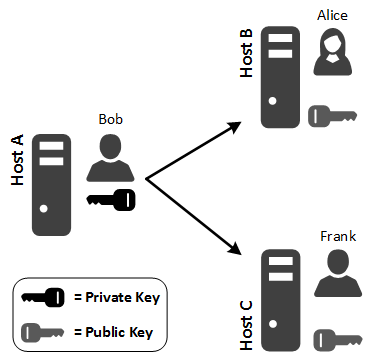
Trust Protection Platform helps you manage which of these users or computers has access to other users or computers.