POST Authorize/Jwt
Obtains an authorization token. The Venafi Authorization End Point (VEDauth) returns a bearer access token and other information. After this call completes, place the access_token in the header of your REST call. Your client can reuse the same token until it expires. As necessary, your client should track the expiration time and use the refresh token to get a new one. On exit, your client can revoke the token.
CAUTION Secure your bearer tokens. Do not share tokens with other integrations. When processing completes, your integration can manage the grant by calling GET Revoke/Token.
Prerequisites
Register an API Integration and give the caller access. Use the scope and other information from the integration. For more information, see Setting up access token authentication.Create a JWT mapping to map JWT tokens to a Trust Protection Platform user. See OAuth JWT mapping endpoints.
Requirements
The caller is not required to have any special permissions.
Headers
Content type: Content-Type:application/json.
- No bearer access token is necessary for this API call.
Parameters
In the request URL, specify vedauth. For example, POST https://tpp.venafi.example/vedauth/authorize/oauth. All parameter names are case sensitive.
Name | Description |
|---|---|
Case sensitive. The value must match the Client ID in the API integration. For more information, see Setting up access token authentication. | |
jwt | The entire JWT token. |
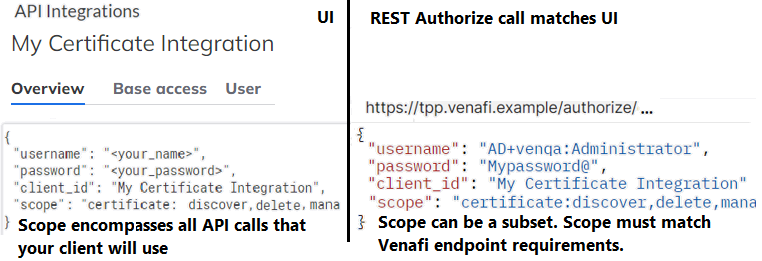
scope | The set of scopes and restrictions for the client_id. The set must:
When getting a token via an Authorize call, you can use the entire scope from the UI API integration OR a subset of the scopes. Check your syntax:
|
Returns
For invalid requests, this method returns Error and a message.
On success, the Authorization server returns a HTTP 200 and the following data that applies to the Trust Protection Platform user.
Name | Description |
|---|---|
HTTP 200 | For valid requests, Authorize/Oauth returns a HTTP 200 message; and the following data:
|
HTTP 400 | If the response is HTTP 400, a generic error appears with a customized description for this particular endpoint.
|
HTTP 401 | If there are authentication errors, this API call returns a HTTP 401; it includes one of the following:
|
Example: Use the correct scope; get a bearer token
Request
POST /vedauth/Authorize/Jwt HTTP/1.1
Host: tpp-server-url
Content-Type: application/json
{
"client_id": "VenafiCodeSignClient",
"scope": "codesignclient",
"jwt": "eyJhbGciOiJSUzI1NiI..."
}Response
HTTP/1.1 200 OK
{
"access_token": "7F71xjzl99T2hNUwy5l8Fw==",
"refresh_token": "Mxl4x5E6t0I9Ph06v69H6g==",
"expires_in": 7775999,
"expires": 1639342751,
"token_type": "Bearer",
"scope": "Certificate:delete,discover,manage",
"identity": "local:{a3f32838-c654-49fb-befe-b9d44336ffe0}",
"refresh_until": 1663102751
}