Creating an LDAP connection
You can use the Venafi Configuration Console to create and view LDAP connections. A connection allows Trust Protection Platform to read User and Group data directly from an LDAP Identity Provider.
The Venafi LDAP Identity Wizard makes a connection from Trust Protection Platform to an LDAP Identity Provider. After the LDAP Identity Wizard completes, only the LDAP users and groups you specify can log in and use Trust Protection Platform based on assigned object permissions.
Trust Protection Platform supports LDAP identity object connections to providers using any of the following Internet protocols:
- IPv4 or IPv6-only connections
- IPv4 or IPv6 dual-stack (DS) connections
To create an LDAP connection
- If you have not already done so, download and install the certificates required to establish an SSL connection with the LDAP server. If you are using the ODSEE vendor for LDAP, you can configure the LdapVendor.Oracle-DSee-11g.xml file to match your environment. For additional information about configuring for other vendors, contact Product Support.
- Remote into the Trust Protection Platform server as a master administrator.
- From the Windows Start menu, click Venafi Configuration Console.
- In the left pane of VCC, click Connectors.
-
In the Actions pane, click LDAP Connector.
-
On the Welcome page, click Next and then log in with your credentials.
- On the Before You Begin page, read the requirements, and then click Next.
- On the Connection Information page, configure the connection between Trust Protection Platform and the LDAP Identity Provider, and then click Next.
Parameter name
Description
Name / Address A fully qualified DNS host name or IP address of the LDAP directory that requires connectivity to Trust Protection Platform. Port The port number for the connection between Trust Protection Platform and the LDAP Identity Provider. The default port is 636 for Lightweight Directory Access Protocol over TLS/SSL. Timeout The maximum number of seconds to search the provider for identity information. Encryption The kind of encryption to use between Trust Protection Platform and the LDAP Identity Provider:
- No Encryption: No encryption. (Not recommended).
- Use SSL Encryption (ldaps://): The encryption is LDAP over Secure Socket Layer (SSL).
- Use StartTLS Extension: The extension to serialize secure and plain requests against the LDAP server on a single connection.
Disable certificate revocation check
(Optional) Bypass checking the revocation list to determine whether the encryption certificate is revoked.
Allow anonymous binds
(Optional) Retrieve the initial binding context to the identity provider. If this option is cleared, the wizard connects via the user name and password that you supply on the next screen of the wizard.
To retrieve the required naming contexts, the wizard anonymously binds only for the purpose of reading the rootDSE. All subsequent actions performed by the wizard will always perform a user bind.
Use 'Member Of' for group membership resolution
(Optional) Allow group membership resolution.
Disable user and group search validation by wizard
(Optional) Bypass validating the users and groups.
-
On the Authentication Credentials page, specify the required user Distinguished name (DN) and password of the Identity provider, and then click Next. For example, the User DN: cn=Admin,dc=odsee-qa,dc=venqa,dc=venafi,dc=com.
TIP If you get an error that an LDAP vendor cannot be determined and that there's no available map was found, see the How To: Create new LDAP vendor map for new LDAP provider KB article.
-
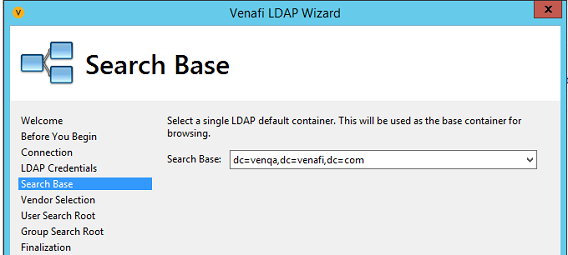
On the Search Base page, select the Default container from the list to search for user and group folders, and then click Next. No folders higher in the tree than this folder will be visible in future searches.
-
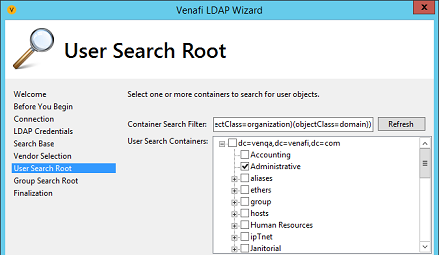
On the User Search Root page, type a folder search value in the Container Search Filter box, and then click Refresh. For example,
(|(objectClass=organizationalUnit)(objectClass=organization)(objectClass=folder))The results only list the User Classes list and the Group Search Expressions that are adaptable. The Remaining fields are read-only.
-
Select the user containers to include in the search. and then click Next.
- On the Group Search Root page, do one (or both) of the following, and then click Next:
- (Optional) if you want your selections from the previous screen to be replicated in the Group Search Containers tree, select Match User Search Containers.
(Optional) In the Group Search Containers tree, expand and select the groups to include in the search.
The users and groups in the folders you select will be visible in the new LDAP connection that you are creating.
-
On the Finalization page, specify the following values as appropriate, and then click Next.
Parameter name
Description
Object Name A name for your new LDAP Identity Provider object that appears in the Identity tree and in VCC. Choose a unique name that can help your administrators more easily recognize the providers. Friendly Name A name for internal use by Trust Protection Platform. Type a brief name with only alphanumeric characters and spaces. The Friendly Name can match the Object Name. However, the Friendly Name must be unique for this object type in Trust Protection Platform. Rank The search order for this identity provider. If there are multiple identity providers, Trust Protection Platform searches for credentials starting with the lowest number first.
In the case where there are identical names, such as Administrator, Trust Protection Platform finds the first instance. If the password is incorrect, no additional searches occur in the other providers.
What's next
- Restart the Trust Protection Platform and Venafi Log Server services as well as any Web or Policy Tree sessions.
- (Optional) If you want to log into Policy Tree as an LDAP user, restart the IIS server that is running on your Trust Protection Platform server. You can use the iisreset command to restart the IIS server.
- Assign groups and users who need access to the new provider.
- To review or update basic settings from VCC, click Properties.