Granting access to CyberArk Application Identity Manager (AIM)
Granting access when using AIM/AAM agent to retrieve secrets
-
Add the credential provider of the AIM/AAM as a Safe Member.
For example: Prov_<hostname of the machine where AIM/AAM is installed>.
These provider objects MUST have these permissions to the CyberArk Safe:
-
Service Account: Select View Safe Members permission and access to the PVWA interface
-
End user account: Select Retrieve accounts or Use accounts.
-
TPP Application ID: Select Retrieve accounts
-
Windows AIM/AAM Agent credential provider (Prov_<hostname> one): Select Retrieve accounts, List accounts and View Safe Members
-
- Click Save after setting permissions for each object.
Granting access when using Central Credential Provider to retrieve secrets
-
Add the credential provider of the AIM/AAM as a Safe Member.
For example: Prov_<hostname of the machine where AIM/AAM is installed>.
These provider objects MUST have these permissions to the CyberArk Safe:
-
Service Account: Select View Safe Members permission and access to the PVWA interface
-
End user account: Select Retrieve accounts or Use accounts.
-
TPP Application ID: Select Retrieve accounts
-
CCP credential provider (Prov_<hostname> one): Select Retrieve accounts, List accounts and View Safe Members
-
- Click Save after setting permissions for each object.
-
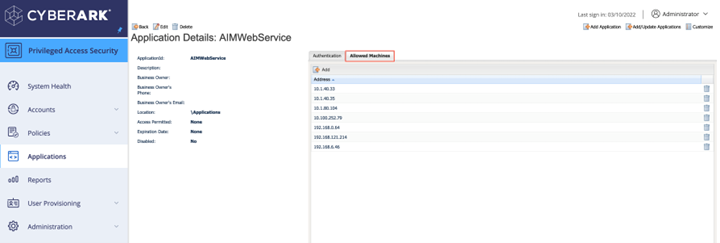
Add the IP address or FQDN of the machine where you installed the CCP in the Allowed Machines tab of the AIMWebService application.
-
The machine where TPP will retrieve CyberArk accounts (secrets) should be allowed to use the TPPApp application in the CyberArk PVWA.
-
On the TPP server the following URL can be used in any web browser in order to test the account (secret) retrieval from the CyberArk Vault (TPP server should be added to the Allowed Machines on the TPPApp application)
https://<CCP Web Sevice URL> /api/Accounts?AppID=<application id>&Safe=<safe name>&Object=<account name to be retrieved>
For example:
https://webservices.example.com /AIMWebService/api/Accounts?AppID=TPPApp&Safe=TestSafe&Object=test_account
Response:
You should retrieve the account's secret in the response's 'Content’ parameter:
"Content": "retrieved_password",
"CreationMethod": "PVWA",
"DeviceType": "Network Device",
"Safe": "TestSafe",
"Name": "test_account",
"Folder": "Root",
"PasswordChangeInProcess": "False"
}