iControl considerations and background
This topic provides additional information about iControl compatibility and related background information.
iControl compatibility issues caused by F5
The following table shows the versions of iControl that have known compatibility issues caused by specific F5 bugs:
|
iControl Version |
Trust Protection Platform Error |
Related F5 Error |
Additional Notes |
|---|---|---|---|
|
11.0.0 through 11.2.0 |
N/A |
F5 Bug 364825: SSL private keys that are stored in the FIPS module are not synchronized during ConfigSync operations. https://support.f5.com/kb/en-us/solutions/public/13000/900/sol13929.html |
This has been fixed in 11.2.1. |
|
11.5.4 HF2 |
Error - 0107149e:3: Virtual server virtual_server_name has more than one clientssl/serverssl profile with same server name. |
F5 Bug 614675: iControl SOAP API call "LocalLB::ProfileClientSSL::create_v2" creates invalid profile |
No GA hotfix as of November 2016. To work around this issue, create SSL profiles manually and then use Trust Protection Platform only to update the certificate, key, and chain of existing SSL profiles. |
|
11.5.4 HF2 and 12.0.0 through 12.1.1 HF2 |
Install Private Key (private_key_name) failed with error: Exception caught in Management ::um:iControl:Management/KeyCertificate::key_import_from_pem() 01020066:3: The requested Certificate Key File (private_key_file_name) already exists in partition partition_name. |
F5 Bug 614865: The BIG-IP system may ignore iControl calls to overwrite an existing key or certificate https://support.f5.com/kb/en-us/solutions/public/k/70/sol70340015.html |
No GA hotfix as of November 2016. This issue causes minimal impact on Trust Protection Platform 25.1 because the need to use the "overwrite" functionality has been minimized by comparing certificates when a name collision occurs. |
|
12.0.0 through 12.0.0-HF2 |
F5 Onboard Discovery out of memory error: "Exception caught in Management::urn:iControl:Management/ KeyCertificate::certificate_export_to_pem()" |
F5 Bug 564427: iControl SOAP: memory leak in Management::KeyCertificate::get_certificate_list_v2 https://support.f5.com/kb/en-us/solutions/public/k/84/sol84349750.html |
This has been fixed beginning with 12.0.0-HF3. https://support.f5.com/kb/en-us/solutions/public/k/84/sol84349750.html |
|
12.0.0 |
Install Certificate Chain (ca_bundle_name) failed with error: Unknown error 16908390 |
F5 Bug 563760-1: iControl call certificate_add_pem_to_bundle fails with the message that the certificate file already exists in the partition |
This has been fixed beginning with 12.1.0. |
|
13.1.0 through 13.1.0.8 13.1.1.0 through 13.1.1.4 14.0.0 through 14.0.0.4 14.1.0 through 14.1.0.2 |
The operation has timed out. |
|
Results in extremely slow provisioning performance or fatal timeout errors when the target F5 is hosting hundreds of certificates. Timeout errors seem to require 2,000 or more certificates in the partition. NOTE F5 has not yet made a fix generally available for either of these bugs; therefore, if this issue affects you, please contact F5 Support to obtain an engineering hot fix. |
The FIPS synchronization issue with versions 11.0.1 through 11.2.0 cannot be detected by Trust Protection Platform. Once provisioned, everything appears to have been installed and synchronized correctly. However, an SSL session on the F5 node that should have been synchronized to will fail, as the private key was not actually installed or updated. This is an issue outside of the control of Trust Protection Platform and it is not an issue in iControl versions 11.2.1 or higher.
Floating self-IP support
If you configure your F5 LTM Advanced in Trust Protection Platform with the Floating Self-IP, it always provisions to the Active node which reduces the number of device objects you need to configure in Trust Protection Platform. The following illustration shows an overview of how the Floating Self-IP works with a pair of F5s.
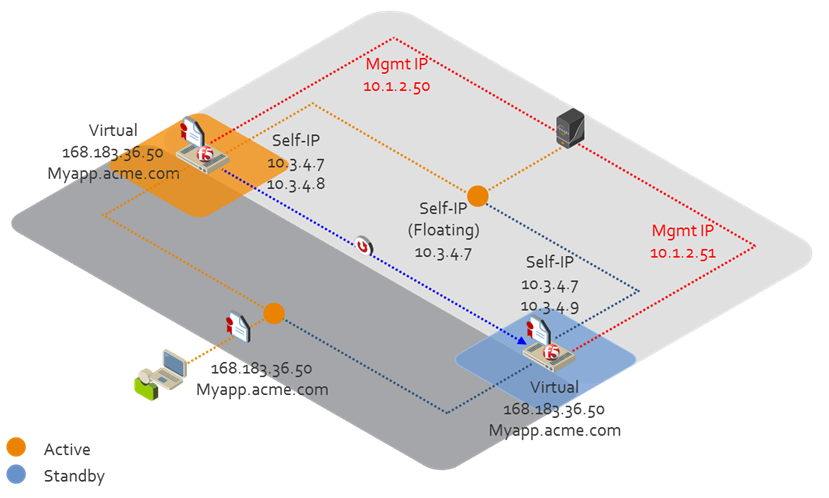
The F5 LTM Advanced driver will continually check the host where it is provisioning. This ensures that if a fail over or other change on the host occur that provision can be stopped and an error event log triggered.
Provisioning the iControl Management Certificate
If you want to provision the iControl management session certificate, there is a configuration option in the F5 LTM Advanced driver. The following graphic shows the configuration option in the driver and the iControl console where the management certificate will be installed:
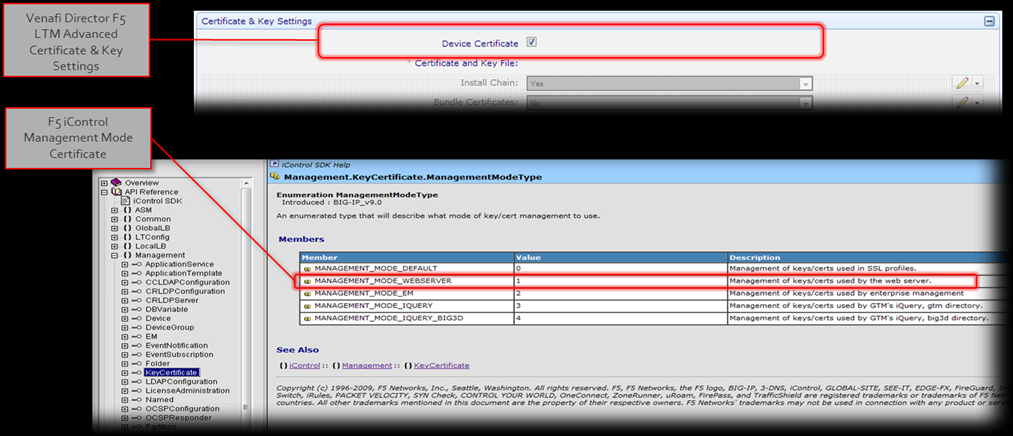
Certificate file naming
It is necessary for the F5 LTM driver to manage the names of the certificate files in order to provide a workable method for certificate renewal, file replacement, disassociation of the old cert with the profile and association of the new certificate with the profile. This naming method follows similar rules as other provisioning drivers that control the file names. The F5 iControl API has a 63 character file name limitation. Automated file naming will be handled as follows:
Original common name:
- www.qa.departmentname.mydomain.net
Trust Protection Platform-generated names:
- www.qa.departmentname.mydomain-1234567.crt
- www.qa.departmentname.mydomain-1234567.key
There are 55 characters available for the common name, 1 character for a dash and 7 characters for the first 7 digits of the certificate's serial number. The common name is truncated from the permission side, if necessary. If the serial number is less than 7 characters, it is prefixed (or padded) with zeros. For example, "SN: 1234" is given a prefix to become "-0001234").