Managing applications using HSM-protected keys and Venafi Advanced Key Protect
Hardware security modules (HSMs) offer a way to provide a higher level of security by generating private keys within a protected domain from which they're never permitted to leave. This means that an attacker would have to do all traffic decryption work from the application server they compromised, which would then put themselves at much greater risk of being detected.
Interfacing an application server with an HSM requires additional software, configuration, and expense.
HSMs are generally reserved for protecting the most mission-critical applications and those that manage highly sensitive data. Venafi can automatically process generating keys inside Thales SafeNet Luna SA and Entrust nShield HSMs using the following provisioning drivers:
- Apache
- CAPI
- JKS
Using remote key generation via an application driver to an HSM allows the HSM to complete the full certificate lifecycle. This remote generation requires that target devices have the necessary HSM client software installed and properly configured.
EXAMPLE The following diagram provides an overview of how you configure your HSM using Trust Protection Platform, an application server (running Apache, Java, or IIS), your HSM client utility and HSM server, and your CA.
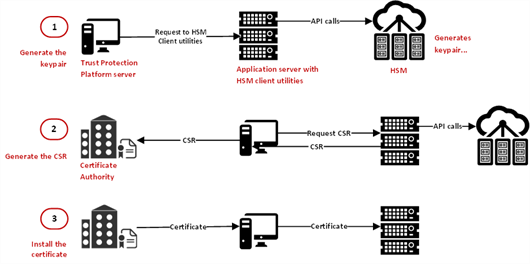
-
Execute command to generate keypair inside the HSM by Trust Protection Platform using your HSM's client utilities and is remotely executed from the Apache/Java/IIS host (the Application server).
-
Execute command to generate CSR on the application server (Apache/Java/IIS host) using your HSM's client utilities and then executed, retrieved, and submitted by Trust Protection Platform to the CA.
-
A certificate is issued by the CA and then retrieved and provisioned by Trust Protection Platform to the application server (Apache/Java/IIS host).
IMPORTANT If you want to configure remote key generation using an HSM, you must activate Venafi Advanced Key Protect, an optional add-on feature to Venafi Trust Protection Platform. For more information, see Venafi Advanced Key Protect.
Normally remote generation only supports one certificate to one application. If you want to install a certificate to many locations, the HSM can do central generation. However, if you are an Advanced Key Protect customer and have HSM connected Apache installations, we do support installing a single certificate to many Apache servers and making sure the Apache is configured to access the private key on the HSM properly. For special configuration information, see Configuring HSM-based remote key generation.
DID YOU KNOW? In asymmetric encryption, security relies upon private keys remaining private. Limiting access to private keys is essential to ensuring that network communications between client and server are secure and protected. This is typically done by setting permissions on keystore files at the operating system level of the computer hosting the certificate and by applying password-based encryption on the keystore itself.
Although this method protects the private key from unauthorized access, it does not prevent a privileged user (or an attacker who has stolen a privileged user’s credentials) from exfiltrating the keystore from the computer and using readily available password-cracking methods to obtain the private key. The possessor of a stolen private key can decrypt communications between the client and server putting sensitive data at risk.