CyberArk user and password integration requirements
Multiple CyberArk users are needed by Trust Protection Platform when interacting with CyberArk. Use the table below to help you implement the required access in CyberArk.
|
CyberArk role |
Action in Trust Protection Platform |
Required CyberArk permissions (for each safe) |
|---|---|---|
|
End User This is a user created in CyberArk for Trust Protection Platform users who need an application or server to authenticate with CyberArk. |
You must provide CyberArk credentials that have access to the safe whenever you create a CyberArk Username Password credential. |
Use accounts or Retrieve accounts NOTE User may be granted access individually or via group membership. Access may not be granted using Object Level Access Control (OLAC). A reason cannot be required for the effective Master Policy to access the password for an account. |
|
Application |
For Trust Protection Platform to use when it retrieves account passwords from a safe. |
Retrieve accounts |
|
Authorization User |
For Trust Protection Platform to verify that the Actual User is authorized to create Username Password credentials. |
View Safe Members |
|
Providers |
Access required by the Application Identity Manager (AIM) installed on each Trust Protection Platform server. |
Retrieve accounts, List accounts, and View Safe Members. |
CyberArk's Safe Members permission panel
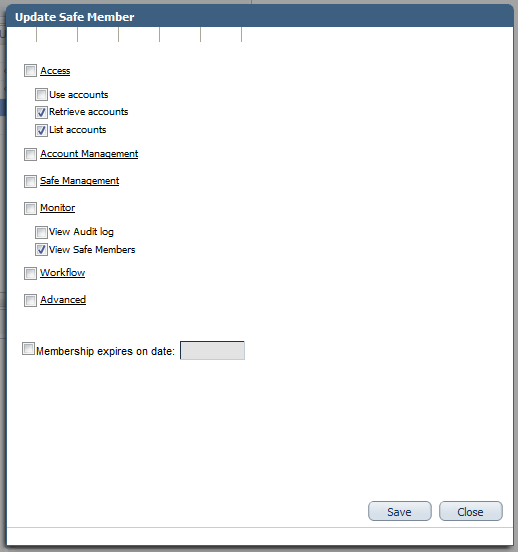
NOTE For information on the settings in the Update Safe Member dialog box, please refer to the CyberArk documentation.