Define allowed signing applications
Venafi CodeSign Protect allows you to restrict what code signing applications are allowed to be used in code signing projects. In addition, you can group applications together into collections. Once the applications and collections are defined, owners of code signing projects can add them to their projects.
NOTE Defining allowed signing applications is an optional restriction. If you don't define any applications, then all signing applications are allowed.
You can identify specific applications using any combination of the following properties:
- Application Checksum
- Authenticode Subject
- Authenticode Issuer
- Client Filesystem Location
- Command Line Regex
Add a code signing application
- Open Signing Applications in the Venafi Code Signing node.
- In the Actions panel, click Add Code Signing Application.
-
Enter a name for the application you are adding.
The name you enter here will appear in the Aperture interface when setting up code signing projects.
The Properties dialog for your new application entry opens.
-
Enter a Description for this application.
-
Complete any of the remaining fields to implement restrictions.
Click the Load button to select a signing application on your hard drive. The Application Checksum, Authenticode Subject, Authenticode Issuer, and Client Filesystem Location fields will populate with the values from that application. Once populated, you can edit or delete the field values as necessary.
To use the Command Line Regex field, refer to Using the Command Line Regex field for instructions.
IMPORTANT Signing applications must meet all the properties you specify in order to sign code.
- Click OK.
Add a Collection
- In the Actions panel, click Add Collection.
- Give the collection a name and then click Create. This adds the collection as a sub-node under Signing Applications and opens that note.
- In the Actions panel, click Add items to collection.
-
From the drop-down list, search for the applications you want to add to this collection, and move them from Results to Selected.
TIP To see all applications, just enter an asterisk * in the Search field.
- Click Close, and then click Add.
Using the Command Line Regex field
The Command Line Regex field allows you to enter a regex that the signing command must match in order for signing to occur. Whereas the other options allow you to specify a certain signing application, the regex field allows you to set specific requirements that the signing command itself must meet.
When you click in the Command Line Regex field, the Regular Expression Assistance window opens. While it's not required to use this Window, it can be helpful to ensure that your regex meets your requirements. Using this Window, you can craft your regex, and the test specific signing commands to see if they would be allowed.
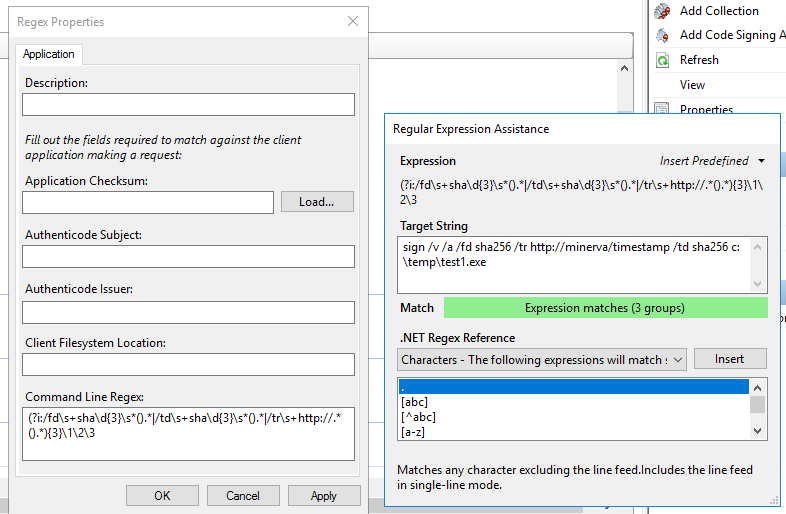
Tips on using the Regular Expression Assistance window
-
Anything that you enter into the Command Line Regex box will be mirrored in the Expression space in the assistance window.
-
You can use the .NET Regex Reference to help craft the regex. Anything you Insert from the Reference will populate in the Command Line Regex field.
-
The Target String field allows you to enter a sample signing command. If the string matches the regex, you'll see a green box stating Expression matches. Otherwise, the box will be red stating Expression does not match.
-
The Insert Predefined drop-down includes two sample regex expressions that you can use to get started. The two samples are:
-
Signtool with Timestamp
(?i:/fd\s+sha\d{3}\s*().*|/td\s+sha\d{3}\s*().*|/tr\s+http://.*().*){3}\1\2\3This regex enforces the following:
-
The
/fd,/td, and/trswitches must all be included, but can be in any order -
The
/fdand/tdswitches must be followed byshaplus 3 digits (for examplesha256) -
The
/trswitch must be followed byhttp://
The sample string,
sign /v /a /fd sha25 /tr http://timestamp-server /td sha256 c:\temp\test1.exe, meets these criteria. -
-
Jarsigner with Timestamp
(?i:-tsa\s+http:)This regex enforces the
-tsaflag followed byhttp:The sample string,
jarsigner -verbose /Users/codesign/tosign/test.jar Sample-Development-Environment -tsa http://minerva/timestamp -keystore NONE -storetype PKCS11 -certs -storepass none -providerclass sun.security.pkcs11.SunPKCS11 -providerArg /Users/codesign/venafipkcs11.conf, meets the criteria.
-
You can also use this pre-configured online regex tester.
NOTE Limitations:
-
There is not any command line detail for applications like PowerShell and excel. The work around for both of these is to use signtool.
-
The Command Line Regex option is not available to use with GPG or TKTokenDriver.